Report: Decathlon Employee Data Leak Exposed by Hacker in Web Forum in 2023

A hacker shared the data leaked of a previously reported breach involving nearly 8,000 Decathlon employees and customers around the globe.
The vpnMentor research team found an online forum post exposing stolen information from French sporting goods retailer Decathlon. The post was published on September 7, 2023.
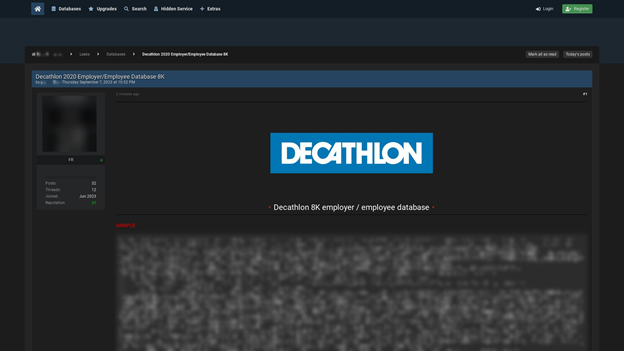 Screenshot of the post exposing Decathlon’s employer/employee database
Screenshot of the post exposing Decathlon’s employer/employee database
The forum user posted a 61-MB database allegedly belonging to Decathlon. According to the post, the database contains the personally identifiable information (PII) of around 8,000 Decathlon employees.
The exposed information supposedly included:
- Full names
- Usernames
- Phone numbers
- Email addresses
- Countries and cities of residence
- Authentication tokens
- Photos
vpnMentor, in its capacity as cybersecurity researchers, immediately reached out to Bluenove and Decathlon to report our discovery of the leaked data on the web forum. Bluenove replied on September 18, 2023, acknowledging the existence of copies of the database that are circulating on darknet forums. The vpnMentor team corresponded with them and proactively offered tips on mitigating the damage in case of further leaks.
Below is a breakdown of the findings:
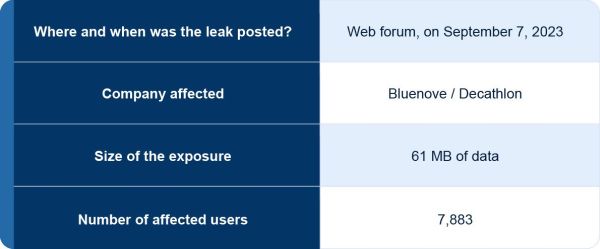
Upon closer inspection of the data posted on the forum, our research team found that the stolen information appeared to match the Decathlon employee data leak that vpnMentor team previously found and reported in 2021.
While we no longer have the data samples from the original leak incident due to our retention policy, our report from before shows that the data shared in the sample posted by the hacker is consistent with the data we found two years prior. This confirms that the recently shared database is authentic.
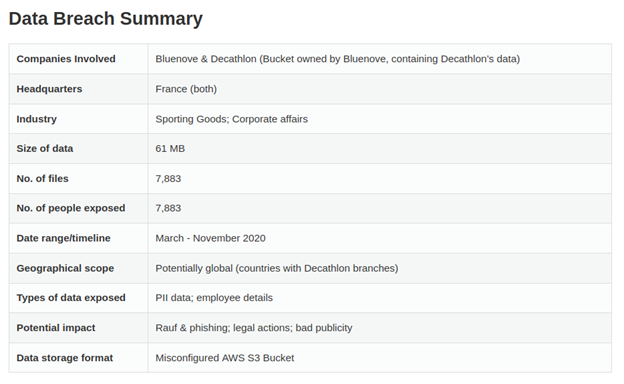 Screenshot of the summary of our report on the 2021 Decathlon data leak
Screenshot of the summary of our report on the 2021 Decathlon data leak
In our original report, we did not reveal the actual format and structure of the data, and the samples we shared were pre-formatted to make them more readable. This means that the forum member who shared the data could not have copied the details from our publication to fake the data.
The breach involved tech and consulting company Bluenove, which specializes in “massive collective intelligence.” The company partnered with Decathlon for the latter’s Vision 2030 campaign, collecting information from employees and customers through a survey.
The data Bluenove gathered was stored in a misconfigured Amazon Web Services (AWS) S3 bucket. vpnMentor detected the leak on March 9, 2021. The research team immediately reached out to Bluenove and AWS to report the discovery. The leak was eventually addressed and fixed on April 13, 2021, after our team’s correspondence with Decathlon.
However, it appears that at least one attacker was able to acquire the information prior to the exposed data being secured, potentially even before vpnMentor found the leak.
Neither the original 2021 leak nor this most recent data exposure was in any way the result of a lapse or negligence on Decathlon’s part. The company was not responsible for securing the information gathered from its stakeholders and had no means to determine whether outside actors managed to acquire the data.
Potential Impacts
Since the people affected by the leak were identified as Decathlon employees, malicious actors could use the exposed information to create elaborate phishing campaigns aimed at extracting further compromising or sensitive data.
For instance, a cyberattacker could potentially pose as an official representative of Bluenove or Decathlon, engage with affected individuals, and convince them to provide their social security numbers or other sensitive PIIs. This information could then be used for identity theft and fraudulent financial or government transactions.
Why Companies Need Robust Cybersecurity Practices
Data breaches can severely impact businesses and organizations. Affected stakeholders can be victimized by fraud, identity theft, and various other cyber crimes when their PIIs fall into the hands of malicious actors. This reputational damage can be disastrous for a business’ finances.
Furthermore, once the data is out there, companies cannot get it back. Fixing the security lapse may prevent more hackers from getting the information firsthand, but it does not keep the people who already have it from sharing it with others or continually exploiting it. In this case, for instance, data that was leaked in 2021 resurfaced in 2023, signaling a continued threat of cyber crimes against those whose data was compromised.
To prevent instances similar to the Decathlon/Bluenove leak, here are a few steps companies may take to secure their data:
- Implement proper access rules to prevent unauthorized access to sensitive information.
- Educate employees on standard procedures when processing confidential files.
- Communicate privacy and disclosure policies clearly to all stakeholders.
- Set up and regularly update third-party security software and cloud encryption.
- Set up incident response plans and regularly test their effectiveness to mitigate the damage in the event of leaks and breaches.
vpnMentor conducted an experiment wherein we created a honeypot to determine how quickly external actors can find and access a misconfigured database.
In the experiment, our misconfigured AWS S3 bucket was discovered by outside actors within 20 days. The fake data we placed in the servers were accessed over 700,000 times in 14 months, but no outside actor ever reached out to inform us about the breach. Our honeypot research report details the methodology and results of the experiment, as well as our analyses.
It should be noted that Amazon Web Services and the other cloud storage platforms used in the experiment are not to blame for the misconfigured servers. Amazon, especially, has several warnings in place to prevent misconfiguration. Our team had to manually ignore these warnings and change the default settings to leave our AWS S3 bucket unprotected. This shows that proper server configuration is almost always under the control of users.
What Should You Do if You Think You’re Affected?
If you were a Decathlon employee between March and November 2020, and you suspect that you may have been affected by the leak, the first step is to reach out to the company and inquire about the actions they took to secure your data.
Then, consider reviewing your online and financial accounts to check for suspicious activity. Be wary of unusual login or access requests. If you notice anything odd, immediately implement ways to safeguard your information. For example, you could change your email login credentials.
What Are Clearweb Leaks and Why Should You Care?
Hackers use all corners of the internet to share information, organize cyberattacks, and talk about data breaches. Some of hackers’ preferred channels are clearweb forums. These are online networks that allow users to post information about breaches and leaks. They offer anonymity to their members and have features like paywalling for users who choose to require payment from those who wish to access their shared data.
Clearweb forums are also easier to navigate. Unlike darknets, these open forums do not require users to have technical savvy to access the platforms and post databases. However, this means that cyberattackers can share stolen information faster, putting more individuals at risk of getting their PIIs and sensitive data exposed. Also, since users can effortlessly find and browse these forums, more people can acquire the breached or leaked information.
Our cybersecurity researchers scour popular data breach forums on the clearweb to find the latest cyberattacks, leaks, and breaches.
By reporting on these incidents, we aim to proactively inform potentially affected parties earlier so that they can act quickly to protect their data. Our disclosures are rooted in meticulous research and are intended solely for informational and preventive purposes. They should not be interpreted as accusatory or indicative of negligence on the part of any entity.

